AlphaSOC Network Behavior Analytics
This Integration is part of the AlphaSOC Network Behavior Analytics Pack.#
Overview
Use the AlphaSOC Network Behavior Analysis integration to instantly retrieve alerts from the AlphaSOC Analytics Engine (either from the cloud or an on-premise instance).
Network telemetry is sent to AlphaSOC (primarily DNS and IP events) from Network Behavior Analytics for Splunk, Network Flight Recorder, or direct API integrations, processed, and alerts generated. AlphaSOC is able to flag infected hosts, policy violations, anomalies, and threats requiring attention.
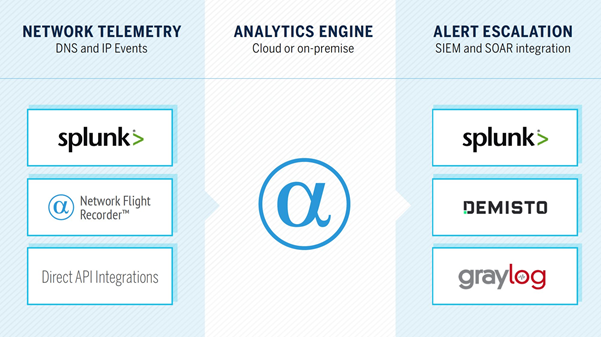
The AlphaSOC Analytics Engine is free to evaluate without restriction for 30 days and you can instantly create an API key within Network Flight Recorder or our Splunk apps to evaluate and use the service.
Configure the AlphaSOC Network Behavior Analysis Integration on Cortex XSOAR
- Navigate to Settings > Integrations > Servers & Services .
- Search for AlphaSOC Network Behavior Analysis.
-
Click
Add instance
to create and configure a new integration instance.
- Name : a textual name for the integration instance.
- AlphaSOC Analysis Engine URL : efaults to cloud .
- AlphaSOC Analysis API Key :your AlphaSOC API key.
- Click Test to validate the API key and connection.
Tune the Integration
Within the settings, the Ignore events below severity field defaults to 3 and is used to filter the content that you are loading into Cortex XSOAR from AlphaSOC. The severity values we use are as follows:
- 5 (critical)
- 4 (high)
- 3 (medium)
- 2 (low)
- 1 (informational).
Critical and high severity alerts include C2 callbacks, ransomware, cryptomining, DNS tunneling, port scanning, DGA traffic, and phishing traffic.
Medium severity alerts have lower fidelity and include beaconing to a suspicious domain, ICMP tunneling, and policy violations, for example, P2P activity, third-party VPN use, potentially unwanted programs or browser extensions present. We recommend leaving this field set to 3, but if you only want to load high-fidelity / high-confidence details of infected hosts into Cortex XSOAR, you can set this to 4.
The Include policy violations field defaults to true and can be set to false if you wish to suppress alerting of items that indicate poor hygiene within the environment, such as potentially unwanted programs (PUPs), unwanted browser extensions, P2P applications (such as BitTorrent), third-party VPN utilities, and remote access software, for example TeamViewer and GoToMyPC.
Test the Integration
When you have telemetry flowing into the AlphaSOC Analytics Engine and the Cortex XSOAR integration configured, you can synthesize malicious traffic and generate alerts for threats including C2 callbacks, DNS tunneling, DGA traffic, and port scanning using our open source Network Flight Simulator utility.
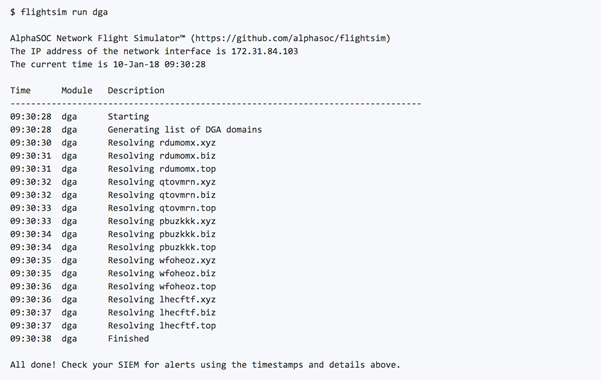
The utility is available for both Windows and Linux, and will generate malicious traffic that in-turn will create incidents within Cortex XSOAR. If you click into the Incidents view, you can review the list.