ThreatConnect (Deprecated)
This Integration is part of the ThreatConnect Pack.#
Deprecated
Use the ThreatConnect v3 integration instead.
Use the ThreatConnect integration to identify, manage, and block threats.
This integration was integrated and tested with ThreatConnect Python SDK v2.
Configure ThreatConnect on Cortex XSOAR
- Navigate to Settings > Integrations > Servers & Services .
- Search for ThreatConnect1.
-
Click
Add instance
to create and configure a new integration instance.
- Name : a textual name for the integration instance.
- Access ID
- Secret Key
- baseUrl
- Default Organization
- ProxyIP (or http://${ip} )
- ProxyPort
- Rating threshold for Malicious Indicators
- Confidence threshold for Malicious Indicators
- Indicator Reputation Freshness (in days)
- Click Test to validate the URLs, token, and connection.
Commands
You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook.
After you successfully execute a command, a DBot message appears in the War Room with the command details.
- Search for an IP indicator: ip
- Search for a URL indicator: url
- Search for a file indicator: file
- Retrieve possible owners from an account: tc-owners
- Retrieve all indicators: tc-indicators
- Get all tags: tc-get-tags
- Tag an existing indicator: tc-tag-indicator
- Get an indicator: tc-get-indicator
- Get all indicators with a specific tag: tc-get-indicators-by-tag
- Add a new indicator: tc-add-indicator
- Create a new incident: tc-create-incident
- Fetch incidents: tc-fetch-incidents
- Associate an indicator to an incident: tc-incident-associate-indicator
- Check domain reputation: domain
- Get incidents related to an indicator: tc-get-incident-associate-indicators
- Update an indicator: tc-update-indicator
- Remove a tag from an indicator: tc-delete-indicator-tag
- Delete an indicator: tc-delete-indicator
- Create a group from a campaign: tc-create-campaign
- Create a group from an event: tc-create-event
- Create a group from threats: tc-create-threat
- Delete a group: tc-delete-group
- Add an attribute to an event: tc-add-group-attribute
- Get a list of events: tc-get-events
- Get all groups: tc-get-groups
- Add a security label to a group: tc-add-group-security-label
- Add tags to a group: tc-add-group-tag
- Get all indicator types: tc-get-indicator-types
- Associate an indicator to a group: tc-group-associate-indicator
- Create a document group: tc-create-document-group
- Retrieve a single group: tc-get-group
- Retrieves the attribute of a group: tc-get-group-attributes
- Retrieves the security labels of a group: tc-get-group-security-labels
- Retrieves the tags of a group: tc-get-group-tags
- Downloads the contents of a document: tc-download-document
- Returns indicators associated with a group: tc-get-group-indicators
- Returns indicators associated with a specified group: tc-get-associated-groups
- Associates one group with another group: tc-associate-group-to-group
1. Search for an IP address indicator
Searches for an indicator of type IP address.
Base Command
ip
Input
| Argument Name | Description | Required |
|---|---|---|
| ip | The IPv4 or IPv6 address. | Required |
| owners | A CSV list of a client's organizations, sources, or communities to which a user has permissions. For example, users with admin permissions can search for indicators belonging to all owners. | Optional |
| ratingThreshold | A list of results filtered by indicators whose threat rating is greater than the specified value. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidenceThreshold | A list of results filtered by indicators whose confidence rating is greater than the specified value. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
Command Example
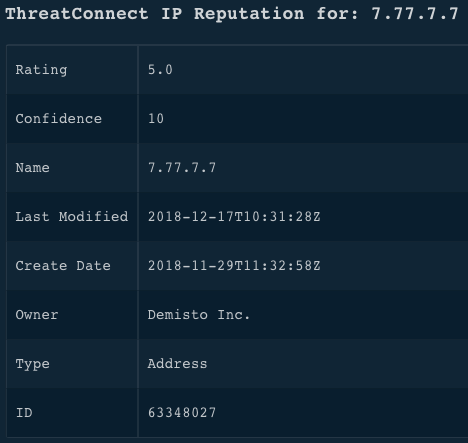
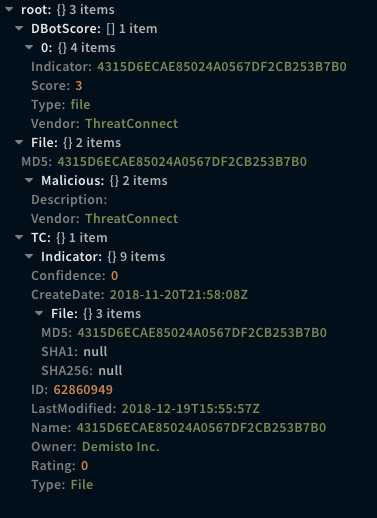
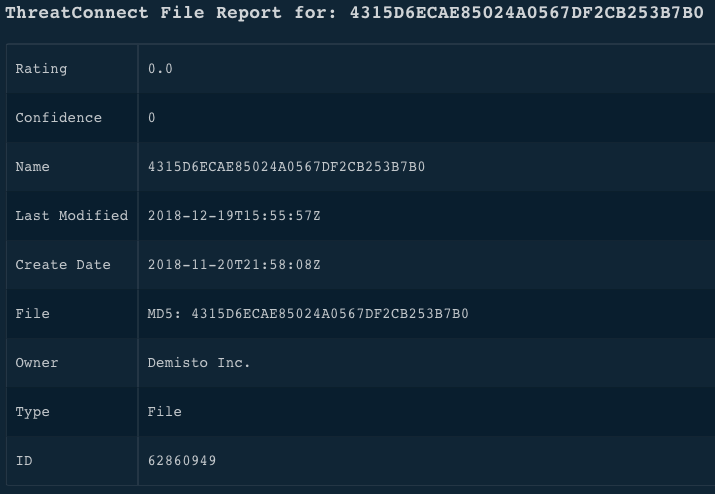
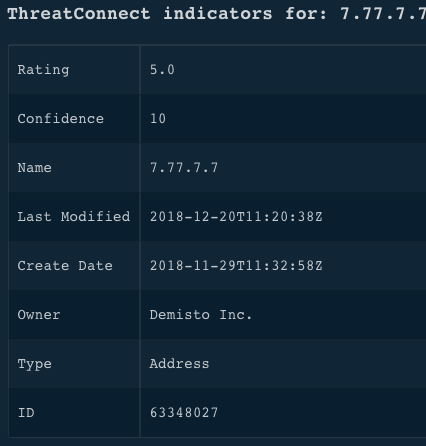
!ip ip=7.77.7.7
Context Example
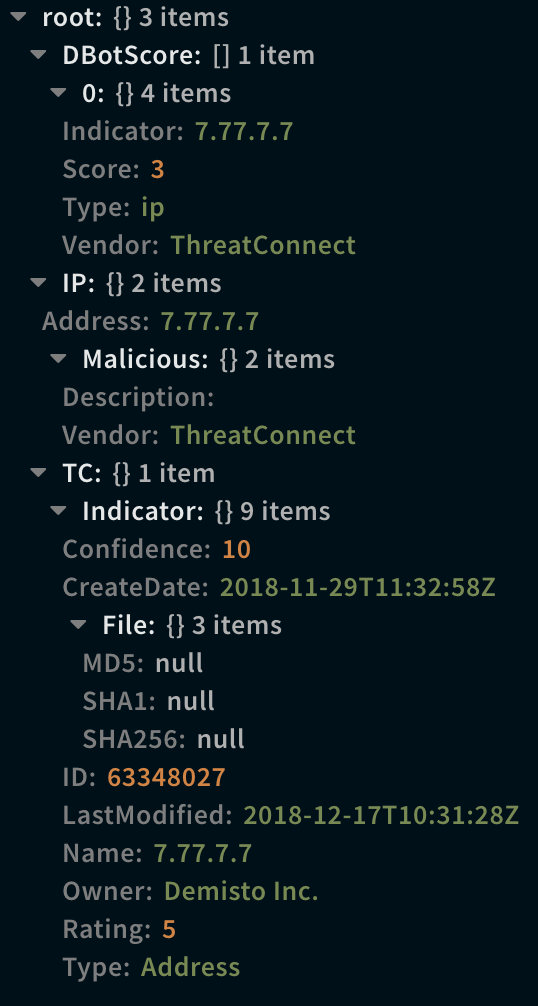
Human Readable Output
2. Search for an indicator of type URL
Searches for an indicator of type URL.
Base Command
url
Input
| Argument Name | Description | Required |
|---|---|---|
| url | The URL for which to search. For example, "www.demisto.com". | Required |
| owners | A CSV list of a client's organizations, sources, or communities to which a client’s API user has been granted permission. For example, "owner1", "owner2", or "owner3". | Optional |
| ratingThreshold | A list of results filtered by indicators whose threat rating is greater than the specified value. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidenceThreshold | A list of results filtered by indicators whose confidence rating is greater than the specified value. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The date on which the indicator was last modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| URL.Data | string | The data of the URL indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
Command Example
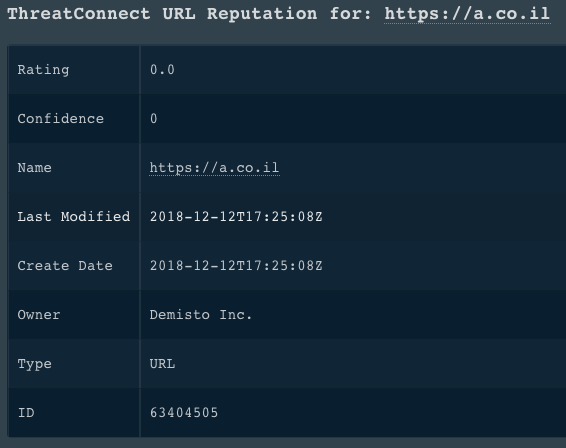
!url url=https://a.co.il
Context Example
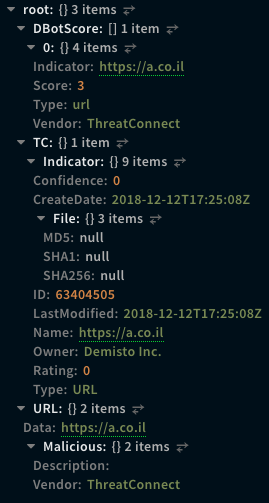
Human Readable Output
3. Search for an indicator of type file
Searches for an indicator of type file.
Base Command
file
Input
| Argument Name | Description | Required |
|---|---|---|
| file | The hash of the file. Can be "MD5", "SHA-1", or "SHA-256". | Required |
| owners | A CSV list of a client's organizations, sources, or communities to which a user has permissions. For example, users with admin permissions can search for indicators belonging to all owners. | Optional |
| ratingThreshold | A list of results filtered by indicators whose threat rating is greater than the specified value. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidenceThreshold | A list of results filtered by indicators whose confidence rating is greater than the specified value. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| File.MD5 | string | The MD5 hash of the indicator. |
| File.SHA1 | string | The SHA1 hash of the indicator. |
| File.SHA256 | string | The SHA256 hash of the indicator. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
Human Readable Output
4. Retrieves all owners for the current account
Retrieves all owners for the current account.
Base Command
tc-owners
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Owner.Name | string | The name of the owner. |
| TC.Owner.ID | string | The ID of the owner. |
| TC.Owner.Type | string | The type of the owner. |
5. Retrieve a list of all indicators
Retrieves a list of all indicators.
Base Command
tc-indicators
Input
| Argument Name | Description | Required |
|---|---|---|
| owner | A list of results filtered by the owner of the indicator. | Optional |
| limit | The maximum number of results that can be returned. The default is 500. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The name of the domain. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
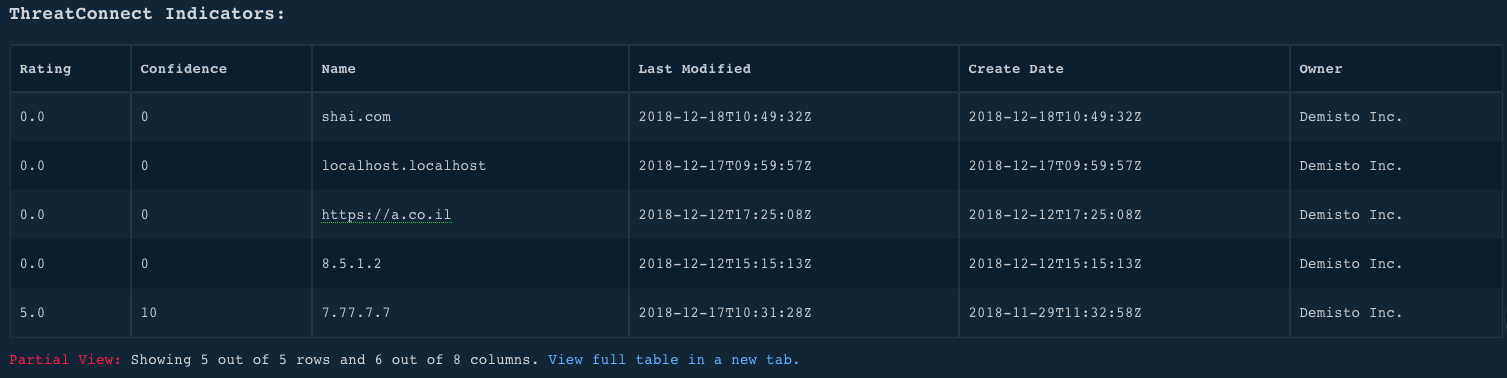
!tc-indicators limit=5
Context Example
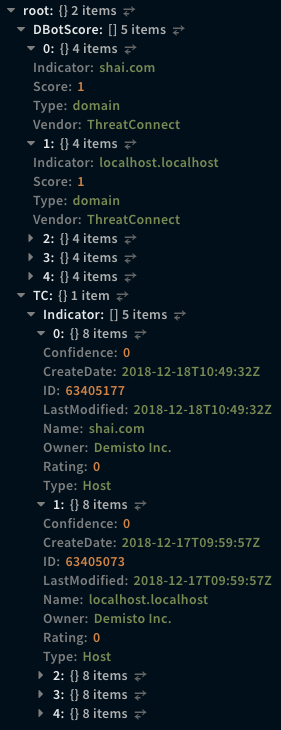
Human Readable Output
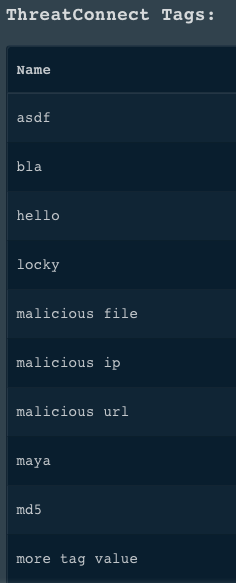
6. Return a list of all ThreatConnect tags
Returns a list of all ThreatConnect tags.
Base Command
tc-get-tags
Input
| Argument Name | Description | Required |
|---|---|---|
| tag | The name of the tag | Required |
| indicator |
The indicator to tag. For example, for an IP indicator, "8.8.8.8".
|
Required |
| owner |
A list of indicators filtered by the owner.
|
Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Tags | Unknown | A list of tags. |
Command Example
!tc-get-tags
Human Readable Output
7. Add a tag to an existing indicator
Adds a tag to an existing indicator.
Base Command
tc-tag-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| tag | The name of the tag. | Required |
| indicator | The indicator to tag. For example, for an IP indicator, "8.8.8.8". | Required |
| owner | A list of indicators filtered by the owner. | Optional |
Command Example
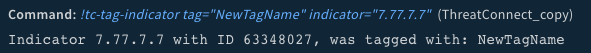
!tc-tag-indicator indicator=7.77.7.7 tag=NewTagName
Human Readable Output
8. Retrieves information about an indicator
Retrieves information about an indicator.
Base Command
tc-get-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator | The name of the indicator by which to search. The command retrieves information from all owners. Can be an IP address, a URL, or a file hash. | Required |
| ratingThreshold | A list of results filtered by indicators whose threat rating is greater than the specified value. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidenceThreshold | A list of results filtered by indicators whose confidence rating is greater than the specified value. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the indicator of the URL. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The domain name of the indicator. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
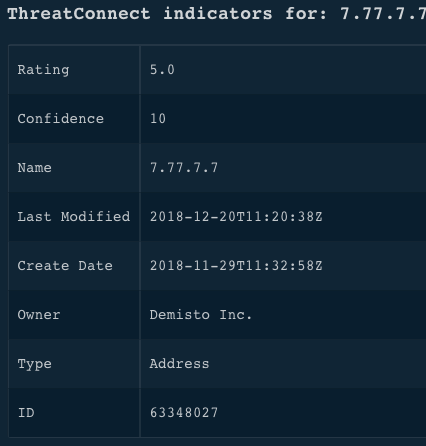
!tc-get-indicator indicator=7.77.7.7
Human Readable Output
9. Fetch all indicators that have a tag
Fetches all indicators that have a tag.
Base Command
tc-get-indicators-by-tag
Input
| Argument Name | Description | Required |
|---|---|---|
| tag | The name of the tag by which to filter. | Required |
| owner | A list of indicators filtered by the owner. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the tagged indicator. |
| TC.Indicator.Type | string | The type of the tagged indicator. |
| TC.Indicator.ID | string | The ID of the tagged indicator. |
| TC.Indicator.Description | string | The description of the tagged indicator. |
| TC.Indicator.Owner | string | The owner of the tagged indicator. |
| TC.Indicator.CreateDate | date | The date on which the tagged indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the tagged indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the tagged indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the tagged indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| DBotScore.Indicator | string | The value assigned by DBot for the tagged indicator. |
| DBotScore.Type | string | The type assigned by DBot for the tagged indicator. |
| DBotScore.Score | number | The score assigned by DBot for the tagged indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| IP.Address | string | The IP address of the tagged indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the tagged indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The domain name of the tagged indicator. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
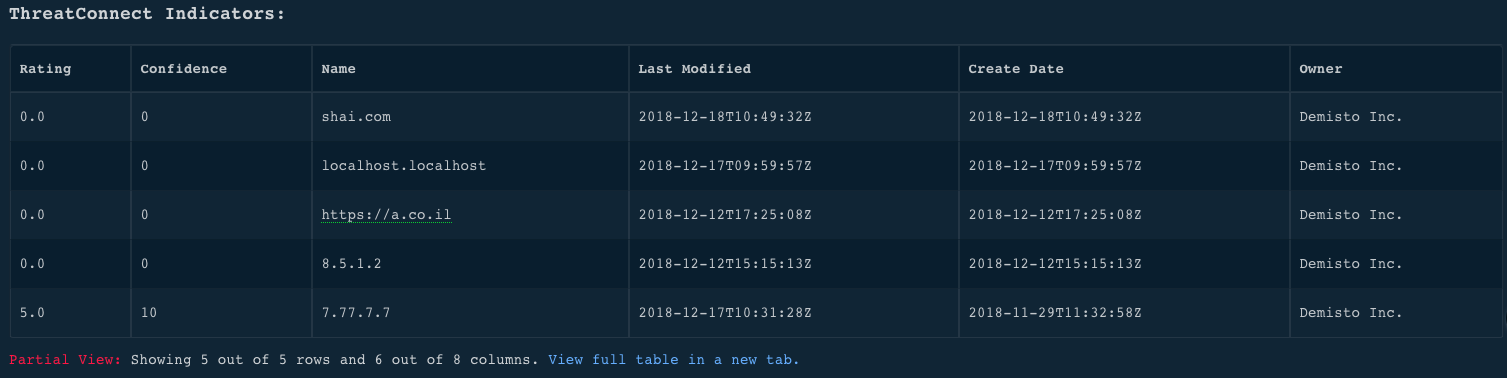
!tc-get-indicators-by-tag tag=NewTagName
Human Readable Output
10. Add a new indicator to ThreatConnect
Adds a new indicator to ThreatConnect.
Base Command
tc-add-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator | The indicator to add. | Required |
| rating | The threat rating of the indicator. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidence | The confidence rating of the indicator. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
| owner | The owner of the new indicator. The default is the "defaultOrg" parameter. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name the indicator. |
| TC.Indicator.Type | string | The type of indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the added indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the added indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The name of the added indicator of the domain. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
!tc-add-indicator indicator="9.9.4.4" rating="2" confidence="87"
Human Readable Output
11. Create a new incident group
Creates a new incident group.
Base Command
tc-create-incident
Input
| Argument Name | Description | Required |
|---|---|---|
| owner | The owner of the new incident. The default is the "defaultOrg" parameter. | Optional |
| incidentName | The name of the incident group. | Required |
| eventDate | The creation time of an incident in the "2017-03-21T00:00:00Z" format. | Optional |
| tag | The tag applied to the incident. | Optional |
| securityLabel | The security label applied to the incident. Can be "TLP:RED", "TLP:GREEN", "TLP:AMBER", or "TLP:WHITE". | Optional |
| description | The description of the incident. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Incident.Name | string | The name of the new incident group. |
| TC.Incident.Owner | string | The owner of the new incident. |
| TC.Incident.EventDate | date | The date on which the event that indicates an incident occurred. |
| TC.Incident.Tag | string | The name of the tag of the new incident. |
| TC.Incident.SecurityLabel | string | The security label of the new incident. |
| TC.Incident.ID | Unknown | The ID of the new incident. |
Command Example
!tc-create-incident incidentName="NewIncident" description="NewIncident" severity="Critical" category="Intrusion" company=Demisto tag=demisto
12. Fetch incidents from ThreatConnect
Fetches incidents from ThreatConnect.
Base Command
tc-fetch-incidents
Input
| Argument Name | Description | Required |
|---|---|---|
| incidentId | The fetched incidents filtered by ID. | Optional |
| owner | The fetched incidents filtered by owner. | Optional |
| incidentName | The fetched incidents filtered by incident name. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Incident | string | The name of the group of fetched incidents. |
| TC.Incident.ID | string | The ID of the fetched incidents. |
| TC.Incident.Owner | string | The owner of the fetched incidents. |
Command Example
!tc-fetch-incidents incidentId=64862
13. Associate an indicator with an existing incident
Associates an indicator with an existing incident. The indicator must exist before running this command. To add an indicator, run the tc-add-indicator command.
Base Command
tc-incident-associate-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicatorType | The type of the indicator. Can be "ADDRESSES", "EMAIL_ADDRESSES", "URLS", "HOSTS", "FILES", or "CUSTOM_INDICATORS". | Required |
| incidentId | The ID of the incident to which the indicator is associated. | Required |
| indicator | The name of the indicator. | Required |
| owner | A list of indicators filtered by the owner. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator associated was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator associated was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| IP.Address | string | IP address of the associated indicator of the file. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the associated indicator of the file. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The name of the indicator of the domain. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
!tc-incident-associate-indicator indicator=46.148.22.18 incidentId=64862 indicatorType=ADDRESSES
Human Readable Output
14. Search for an indicator of type domain
Searches for an indicator of type domain.
Base Command
domain
Input
| Argument Name | Description | Required |
|---|---|---|
| domain | The name of the domain. | Required |
| owners | A CSV list of a client's organizations, sources, or communities to which a user has permissions. For example, users with admin permissions can search for indicators belonging to all owners. | Optional |
| ratingThreshold | A list of results filtered by indicators whose threat rating is greater than the specified value. Can be "0" - "Unknown", "1" - "Suspicious", "2" - "Low", "3" - Moderate, "4" - High, or "5" - "Critical". | Optional |
| confidenceThreshold | A list of results filtered by indicators whose confidence rating is greater than the specified value. Can be "0%" - "Unknown," "1% " - "Discredited", "2-29%" - "Improbable," "30-49%" - "Doubtful," "50-69%" - "Possible", "70-89%" - "Probable," or "90-100%" - "Confirmed". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the of the indicator. |
| TC.Indicator.Type | string | The type of the domain. |
| TC.Indicator.ID | string | The ID of the domain. |
| TC.Indicator.Description | string | The description of the domain. |
| TC.Indicator.Owner | string | The owner of the domain. |
| TC.Indicator.CreateDate | date | The date on which the indicator of the domain was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator of the domain was modified. |
| TC.Indicator.Rating | number | The threat rating of the domain. |
| TC.Indicator.Confidence | number | The confidence rating of the domain. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| Domain.Name | string | The name of the domain. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
Command Example
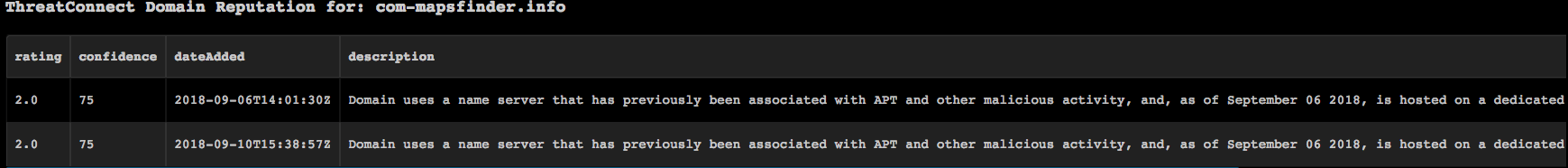
!domain domain=com-mapsfinder.info
Human Readable Output
15. Return indicators related to a specific incident
Returns indicators that are related to a specific incident.
Base Command
tc-get-incident-associate-indicators
ermission 2
Input
| Argument Name | Description | Required |
|---|---|---|
| incidentId | The ID of the incident. | Required |
| owner | A list of indicators filtered by the owner. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the returned indicator. |
| TC.Indicator.Type | string | The type of the returned indicator. |
| TC.Indicator.ID | string | The ID of the returned indicator. |
| TC.Indicator.Description | string | The description of the returned indicator. |
| TC.Indicator.Owner | string | The owner of the returned indicator. |
| TC.Indicator.CreateDate | date | The date on which the returned indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the returned indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the returned indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the returned indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| DBotScore.Indicator | string | The value assigned by DBot for the indicator. |
| DBotScore.Type | string | The type assigned by DBot for the indicator. |
| DBotScore.Score | number | The score assigned by DBot for the indicator. |
| DBotScore.Vendor | string | The vendor used to calculate the score. |
| IP.Address | string | The IP address of the returned indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the returned indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The name of the domain. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
Command Example
!tc-get-incident-associate-indicators incidentId=64862
16. Update the indicator in ThreatConnect
Updates the indicator in ThreatConnect.
Base Command
tc-update-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator | The name of the updated indicator. | Required |
| rating | The threat rating of the updated indicator. | Optional |
| confidence | The confidence rating of the updated indicator. | Optional |
| size | The size of the file of the updated indicator. | Optional |
| dnsActive | The active DNS indicator (only for hosts). | Optional |
| whoisActive | The active indicator (only for hosts). | Optional |
| updatedValues | A CSV list of field:value pairs to update. For example, "rating=3", "confidence=42", and "description=helloWorld". | Optional |
| falsePositive | The updated indicator set as a false positive. Can be "True" or "False". | Optional |
| observations | The number observations on the updated indicator. | Optional |
| securityLabel | The security label applied to the incident. Can be "TLP:RED", "TLP:GREEN", "TLP:AMBER", or "TLP:WHITE". | Optional |
| threatAssessConfidence | Assesses the confidence rating of the indicator. | Optional |
| threatAssessRating | Assesses the threat rating of the indicator. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The domain name of the indicator. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
17. Remove a tag from a specified indicator
Removes a tag from a specified indicator.
Base Command
tc-delete-indicator-tag
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator | The name of the indicator from which to remove a tag. | Required |
| tag | The name of the tag to remove from the indicator. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Indicator.Name | string | The name of the indicator. |
| TC.Indicator.Type | string | The type of the indicator. |
| TC.Indicator.ID | string | The ID of the indicator. |
| TC.Indicator.Description | string | The description of the indicator. |
| TC.Indicator.Owner | string | The owner of the indicator. |
| TC.Indicator.CreateDate | date | The date on which the indicator was created. |
| TC.Indicator.LastModified | date | The last date on which the indicator was modified. |
| TC.Indicator.Rating | number | The threat rating of the indicator. |
| TC.Indicator.Confidence | number | The confidence rating of the indicator. |
| TC.Indicator.WhoisActive | string | The active indicator (for domains only). |
| TC.Indicator.File.MD5 | string | The MD5 hash of the indicator of the file. |
| TC.Indicator.File.SHA1 | string | The SHA1 hash of the indicator of the file. |
| TC.Indicator.File.SHA256 | string | The SHA256 hash of the indicator of the file. |
| IP.Address | string | The IP address of the indicator. |
| IP.Malicious.Vendor | string | For malicious IP addresses, the vendor that made the decision. |
| IP.Malicious.Description | string | For malicious IP addresses, the full description. |
| URL.Data | string | The data of the URL of the indicator. |
| URL.Malicious.Vendor | string | For malicious URLs, the vendor that made the decision. |
| URL.Malicious.Description | string | For malicious URLs, the full description. |
| Domain.Name | string | The domain name of the indicator. |
| Domain.Malicious.Vendor | string | For malicious domains, the vendor that made the decision. |
| Domain.Malicious.Description | string | For malicious domains, the full description. |
| File.MD5 | string | The MD5 hash of the file. |
| File.SHA1 | string | The SHA1 hash of the file. |
| File.SHA256 | string | The SHA256 hash of the file. |
| File.Malicious.Vendor | string | For malicious files, the vendor that made the decision. |
| File.Malicious.Description | string | For malicious files, the full description. |
18. Delete an indicator from ThreatConnect
Deletes an indicator from ThreatConnect.
Base Command
tc-delete-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator | The name of the indicator to delete. | Required |
Command Example
19. Create a group based on the Campaign type
Creates a group based on the "Campaign" type.
Base Command
tc-create-campaign
Input
| Argument Name | Description | Required |
|---|---|---|
| name | The name of the campaign group. | Required |
| firstSeen | The earliest date on which the campaign was seen. | Optional |
| owner | The owner of the new incident. The default is the "defaultOrg" parameter. | Optional |
| description | The description of the campaign. | Optional |
| tag | The name of the tag to apply to the campaign. | Optional |
| securityLabel | The security label of the campaign. For example, "TLP:Green". | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Campaign.Name | string | The name of the campaign. |
| TC.Campaign.Owner | string | The owner of the campaign. |
| TC.Campaign.FirstSeen | date | The earliest date on which the campaign was seen. |
| TC.Campaign.Tag | string | The tag of the campaign. |
| TC.Campaign.SecurityLevel | string | The security label of the campaign. |
| TC.Campaign.ID | string | The ID of the campaign. |
20. Create a group based on the Event type
Creates a group based on the "Event" type.
Base Command
tc-create-event
Input
| Argument Name | Description | Required |
|---|---|---|
| name | The name of the event group. | Required |
| eventDate | The date on which the event occurred. If the date is not specified, the current date is used. | Optional |
| status | The status of the event. Can be "Needs Review", "False Positive", "No Further Action", or "Escalated". | Optional |
| owner | The owner of the event. | Optional |
| description | The description of the event. | Optional |
| tag | The tag of the event. | Optional |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Event.Name | string | The name of the event. |
| TC.Event.Date | date | The date of the event. |
| TC.Event.Status | string | The status of the event. |
| TC.Event.Owner | string | The owner of the event. |
| TC.Event.Tag | string | The tag of the event. |
| TC.Event.ID | string | The ID of the event. |
21. Create a group based on the Threats type
Creates a group based on the "Threats" type.
Base Command
tc-create-threat
Input
| Argument Name | Description | Required |
|---|---|---|
| name | The name of the threat group. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Threat.Name | string | The name of the threat. |
| TC.Threat.ID | string | The ID of the threat. |
22. Delete a group
Deletes a group.
Base Command
tc-delete-group
Input
| Argument Name | Description | Required |
|---|---|---|
| groupID | The ID of the group to delete. | Required |
| type | The type of the group to delete. Can be "Incidents", "Events", "Campaigns", or "Threats". | Required |
23. Add an attribute to a specified group
Adds an attribute to a specified group.
Base Command
tc-add-group-attribute
Input
| Argument Name | Description | Required |
|---|---|---|
| group_id | The ID of the group to which to add attributes. To get the ID of the group, run the tc-get-groups command. | Required |
| attribute_type | The type of attribute to add to the group. The type is located in the UI in a specific group or under Org Config. | Required |
| attribute_value | The value of the attribute. | Required |
| group_type | The type of the group. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.DateAdded | Date | The date on which the attribute was added. |
| TC.Group.LastModified | Date | The date on which the added attribute was last modified. |
| TC.Group.Type | String | The type of the group to which the attribute was added. |
| TC.Group.Value | String | The value of the attribute added to the group. |
| TC.Group.ID | Number | The group ID to which the attribute was added. |
Command Example
!tc-add-group-attribute attribute_type="EXTERNAL ID" attribute_value=123456789 group_id=4406377 group_type=events
24. Return a list of events
Returns a list of events.
Base Command
tc-get-events
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Event.DateAdded | Date | The date on which the event was added. |
| TC.Event.EventDate | Date | The date on which the event occurred. |
| TC.Event.ID | Number | The ID of the event. |
| TC.Event.OwnerName | String | The name of the owner of the event. |
| TC.Event.Status | String | The status of the event. |
Command Example
!tc-get-events
25. Return all groups
Returns all groups, filtered by the group type.
Base Command
tc-get-groups
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of the group. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.DateAdded | Date | The date on which the group was added. |
| TC.Group.EventDate | Date | The date on which the event occurred. |
| TC.Group.Name | String | The name of the group. |
| TC.Group.OwnerName | String | The name of the owner of the group. |
| TC.Group.Status | String | The status of the group. |
| TC.Group.ID | Number | The ID of the group. |
Command Example
!tc-get-groups group_type=events
26. Add a security label to a group
Adds a security label to a group.
Base Command
tc-add-group-security-label
Input
| Argument Name | Description | Required |
|---|---|---|
| group_id | The ID of the group to which to add the security label. To get the ID, run the tc-get-groups command. | Required |
| group_type | The type of the group to which to add the security label. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| security_label_name | The name of the security label to add to the group. For example, "TLP:GREEN". | Required |
Command Example
!tc-add-group-security-label group_id=4406377 group_type=events security_label_name=TLP:GREEN
27. Adds tags to a specified group
Adds tags to a specified group.
Base Command
tc-add-group-tag
Input
| Argument Name | Description | Required |
|---|---|---|
| group_id | The ID of the group to which to add the tag. To get the ID, run the tc-get-groups command. | Required |
| group_type | The type of the group to which to add the tag. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| tag_name | The name of the tag to add to the group. | Required |
Command Example
!tc-add-group-tag group_id=4378343 group_type=events tag_name=phishing
28. Returns all indicator types
Returns all indicator types available.
Base Command
tc-get-indicator-types
Input
| Argument Name | Description | Required |
|---|---|---|
| group_id |
The ID of the group to which to add the tag. To get the ID, run the tc-get-groups command.
|
Required |
| group_type |
The type of the group to which to add the tag.
Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents",
"intrusionSets", "reports", "signatures", or "threats".
|
Required |
| tag_name | The name of the indicator. For example, "indicator_type=emailAddresses" where "indicator=a@a.co.il". | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.IndicatorType.ApiBranch | String | The branch of the API. |
| TC.IndicatorType.ApiEntity | String | The entity of the API. |
| TC.IndicatorType.CasePreference | String | The case preference of the indicator. For example, "sensitive", "upper", or "lower". |
| TC.IndicatorType.Custom | Boolean | Whether the indicator is a custom indicator. |
| TC.IndicatorType.Parsable | Boolean | Whether the indicator can be parsed. |
| TC.IndicatorType.Value1Type | String | The name of the indicator. |
| TC.IndicatorType.Value1Label | String | The value label of the indicator. |
Command Example
!tc-get-indicator-types
29. Associates an indicator with a group
Associates an indicator with a group.
Base Command
tc-group-associate-indicator
Input
| Argument Name | Description | Required |
|---|---|---|
| indicator_type | The type of the indicator. To get the available types, run the tc-get-indicator-types command. The indicator must be spelled as displayed in the ApiBranch column of the UI. | Required |
| indicator | The name of the indicator. For example, "indicator_type=emailAddresses" where "indicator=a@a.co.il". | Required |
| group_type | The type of the group. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group. To get the ID of the group, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.GroupID | Number | The ID of the group. |
| TC.Group.GroupType | String | The type of the group. |
| TC.Group.Indicator | String | The name of the indicator. |
| TC.Group.IndicatorType | String | The type of the indicator. |
Command Example
!tc-group-associate-indicator group_id=4406377 group_type=events indicator_type=emailAddresses indicator=a@a.co.il
30. Create a document group
Creates a document group.
Base Command
tc-create-document-group
Input
| Argument Name | Description | Required |
|---|---|---|
| file_name | The name of the file to display in the UI. | Required |
| name | The name of the file. | Required |
| malware | Whether the file is malware. If "true", ThreatConnect creates a password-protected ZIP file on your local machine that contains the sample and uploads the ZIP file. | Optional |
| password | The password of the ZIP file. | Optional |
| security_label | The security label of the group. | Optional |
| description | A description of the group. | Optional |
| entry_id | The file of the ID of the entry, as displayed in the War Room. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.Name | String | The name of the group. |
| TC.Group.Owner | String | The owner of the group. |
| TC.Group.EventDate | Date | The date on which the group was created. |
| TC.Group.Description | String | The description of the group. |
| TC.Group.SecurityLabel | String | The security label of the group. |
| TC.Group.ID | Number | The ID of the group to which the attribute was added. |
Command Example
!tc-create-document-group file_name="sample.pdf" name="sample.pdf" EntryID="13094@b2672a50-1db8-4424-8dcc-2136f4548ce4"
31. Retrieve a single group
Retrieves a single group.
Base Command
tc-get-group
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of group for which to return the ID. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group to retrieve. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.DateAdded | Date | The date on which the group was added. |
| TC.Group.EventDate | Date | The date on which the event occurred. |
| TC.Group.Name | String | The name of the group. |
| TC.Group.Owner.ID | Number | The ID of the group owner. |
| TC.Group.Owner.Name | String | The name of the group owner. |
| TC.Group.Owner.Type | String | The type of the owner. |
| TC.Group.Status | String | The status of the group. |
Command Example
!tc-get-group group_id=4579650 group_type=events
Context Example
{
"TC.Group": {
"DateAdded": "2019-09-18T10:08:37Z",
"EventDate": "2019-09-18T10:08:37Z",
"ID": 4579650,
"Name": "MyTest",
"Owner": {
"ID": 737,
"Name": "Demisto Inc.",
"Type": "Organization"
},
"Status": "Needs Review"
}
}
Human Readable Output
ThreatConnect Group information
| DateAdded | EventDate | ID | Name | Owner | Status |
|---|---|---|---|---|---|
| 2019-09-18T10:08:37Z | 2019-09-18T10:08:37Z | 4579650 | MyTest |
Type: Organization
Name: Demisto Inc. ID: 737 |
Needs Review |
32. Retrieve the attribute of a group
Retrieves the attribute of a group.
Base Command
tc-get-group-attributes
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of group for which to return the attribute. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group for which to return the attribute. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.Attribute.DateAdded | Date | The date on which the group was added. |
| TC.Group.Attribute.Displayed | Boolean | Whether the attribute is displayed on the UI. |
| TC.Group.Attribute.AttributeID | Number | The ID of the attribute. |
| TC.Group.Attribute.LastModified | Date | The date on which the attribute was last modified. |
| TC.Group.Attribute.Type | String | The type of the attribute. |
| TC.Group.Attribute.Value | String | The value of the attribute. |
Command Example
!tc-get-group-attributes group_id=4579650 group_type=events
Context Example
{
"TC.Group.Attribute": [
{
"AttributeID": 20279371,
"DateAdded": "2019-09-18T10:13:06Z",
"Displayed": false,
"GroupID": 4579650,
"LastModified": "2019-09-18T10:13:06Z",
"Type": "External ID",
"Value": "123456789"
},
{
"AttributeID": 20279370,
"DateAdded": "2019-09-18T10:11:37Z",
"Displayed": false,
"GroupID": 4579650,
"LastModified": "2019-09-18T10:11:37Z",
"Type": "External ID",
"Value": "123456789"
},
{
"AttributeID": 20279368,
"DateAdded": "2019-09-18T10:10:07Z",
"Displayed": false,
"GroupID": 4579650,
"LastModified": "2019-09-18T10:10:07Z",
"Type": "External ID",
"Value": "123456789"
},
{
"AttributeID": 20279366,
"DateAdded": "2019-09-18T10:08:38Z",
"Displayed": false,
"GroupID": 4579650,
"LastModified": "2019-09-18T10:08:38Z",
"Type": "External ID",
"Value": "123456789"
}
]
}
Human Readable Output
ThreatConnect Group Attributes
| AttributeID | Type | Value | DateAdded | LastModified | Displayed |
|---|---|---|---|---|---|
| 20279371 | External ID | 123456789 | 2019-09-18T10:13:06Z | 2019-09-18T10:13:06Z | false |
| 20279370 | External ID | 123456789 | 2019-09-18T10:11:37Z | 2019-09-18T10:11:37Z | false |
| 20279368 | External ID | 123456789 | 2019-09-18T10:10:07Z | 2019-09-18T10:10:07Z | false |
| 20279366 | External ID | 123456789 | 2019-09-18T10:08:38Z | 2019-09-18T10:08:38Z | false |
33. Retrieve the security labels of a group
Retrieves the security labels of a group.
Base Command
tc-get-group-security-labels
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of group for which to return the security labels. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group for which to return the security labels. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.SecurityLabel.Name | String | The name of the security label. |
| TC.Group.SecurityLabel.Description | String | The description of the security label. |
| TC.Group.SecurityLabel.DateAdded | Date | The date on which the security label was added. |
Command Example
!tc-get-group-security-labels group_id=4579650 group_type=events
Context Example
{
"TC.Group.SecurityLabel": [
{
"DateAdded": "2016-08-31T00:00:00Z",
"Description": "This security label is used for information that is useful for the awareness of all participating organizations as well as with peers within the broader community or sector.",
"GroupID": 4579650,
"Name": "TLP:GREEN"
}
]
}
Human Readable Output
ThreatConnect Group Security Labels
| Name | Description | DateAdded |
|---|---|---|
| TLP:GREEN | This security label is used for information that is useful for the awareness of all participating organizations as well as with peers within the broader community or sector. | 2016-08-31T00:00:00Z |
34. Retrieves the tags of a group
Retrieves the tags of a group.
Base Command
tc-get-group-tags
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of group for which to return the tags. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group for which to return the tags. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.Tag.Name | String | The name of the tag. |
Command Example
!tc-get-group-tags group_id=4579650 group_type=events
Context Example
{
"TC.Group.Tag": [
{
"GroupID": 4579650,
"Name": "Testing"
}
]
}
Human Readable Output
ThreatConnect Group Tags
| Name |
|---|
| Testing |
35. Downloads the contents of a document
Downloads the contents of a document.
Base Command
tc-download-document
Input
| Argument Name | Description | Required |
|---|---|---|
| document_id | The ID of the document. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| File.Size | Number | The size of the file. |
| File.SHA1 | String | The SHA1 hash of the file. |
| File.SHA256 | String | The SHA256 hash of the file. |
| File.Name | String | The name of the file. |
| File.SSDeep | String | The ssdeep hash of the file (same as displayed in file entries). |
| File.EntryID | String | The entry ID of the file. |
| File.Info | String | The information of the file. |
| File.Type | String | The type of the file. |
| File.MD5 | String | The MD5 hash of the file. |
| File.Extension | String | The extension of the file. |
Command Example
!tc-download-document document_id=1234567
36. Returns indicators associated with a group
Returns indicators associated with a group.
Base Command
tc-get-group-indicators
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of the group for which to return the indicators. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group for which to return the indicators. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.Indicator.Summary | String | The summary of the indicator. |
| TC.Group.Indicator.ThreatAssessConfidence | String | The confidence rating of the indicator. |
| TC.Group.Indicator.IndicatorID | Number | The ID of the indicator. |
| TC.Group.Indicator.DateAdded | Date | The date on which the indicator was added. |
| TC.Group.Indicator.Type | String | The type of the indicator. |
| TC.Group.Indicator.Rating | Number | The threat rating of the indicator. |
| TC.Group.Indicator.ThreatAssertRating | Number | The rating of the threat assert. |
| TC.Group.Indicator.OwnerName | String | The name of the owner of the indicator. |
| TC.Group.Indicator.LastModified | Date | The date that the indicator was last modified. |
Command Example
!tc-get-group-indicators group_id=4579650 group_type=events
Context Example
{
"TC.Group.Indicator": [
{
"Confidence": null,
"DateAdded": "2019-01-03T16:08:07Z",
"GroupID": 4579650,
"IndicatorID": 63441869,
"LastModified": "2019-01-03T16:08:15Z",
"OwnerName": "Demisto Inc.",
"Rating": 2,
"Summary": "a@a.co.il",
"ThreatAssertRating": 2,
"ThreatAssessConfidence": 0,
"Type": "EmailAddress"
}
]
}
Human Readable Output
ThreatConnect Group Indicators
| DateAdded | GroupID | IndicatorID | LastModified | OwnerName | Rating | Summary | ThreatAssertRating | ThreatAssessConfidence | Type |
|---|---|---|---|---|---|---|---|---|---|
| 2019-01-03T16:08:07Z | 4579650 | 63441869 | 2019-01-03T16:08:15Z | Demisto Inc. | 2.0 | a@a.co.il | 2.0 | 0.0 | EmailAddress |
37. Returns indicators associated with a specific group
Returns indicators associated with a specified group.
Base Command
tc-get-associated-groups
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of group. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group. To get the ID, run the tc-get-groups command. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.AssociatedGroup.DateAdded | Date | The date on which group was added. |
| TC.Group.AssociatedGroup.GroupID | Number | The ID of the group. |
| TC.Group.AssociatedGroup.Name | String | The name of the group. |
| TC.Group.AssociatedGroup.OwnerName | String | The name of the owner of the group. |
| TC.Group.AssociatedGroup.Type | String | The type of the group. |
Command Example
!tc-get-associated-groups group_id=4579650 group_type=events
Context Example
{
"TC.Group.AssociatedGroup": [
{
"DateAdded": "2019-01-13T18:13:19Z",
"GroupID": 3594873,
"Name": "NewCampaign",
"OwnerName": "Demisto Inc.",
"Type": "Campaign"
}
]
}
Human Readable Output
ThreatConnect Associated Groups
| GroupID | Name | Type | OwnerName | DateAdded |
|---|---|---|---|---|
| 3594873 | NewCampaign | Campaign | Demisto Inc. | 2019-01-13T18:13:19Z |
38. Associates one group with another group
Associates one group with another group.
Base Command
tc-associate-group-to-group
Input
| Argument Name | Description | Required |
|---|---|---|
| group_type | The type of the group. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| group_id | The ID of the group. To get the ID of the group, run the tc-get-groups command. | Required |
| associated_group_type | The type of group to associate. Can be "adversaries", "campaigns", "documents", "emails", "events", "incidents", "intrusionSets", "reports", "signatures", or "threats". | Required |
| associated_group_id | The ID of the group to associate. | Required |
Context Output
| Path | Type | Description |
|---|---|---|
| TC.Group.AssociatedGroup.AssociatedGroupID | Number | The ID of the associated group. |
| TC.Group.AssociatedGroup.AssociatedGroupType | String | The type of the associated group. |
| TC.Group.AssociatedGroup.GroupID | Number | The ID of the group to associate to. |
| TC.Group.AssociatedGroup.GroupType | String | The type of the group to associate to. |
Command Example
!tc-associate-group-to-group associated_group_id=3594873 associated_group_type=campaigns group_id=4410738 group_type=events
Context Example
{
"TC.Group.AssociatedGroup": {
"AssociatedGroupID": 3594873,
"AssociatedGroupType": "campaigns",
"GroupID": 4410738,
"GroupType": "events"
}
}
Human Readable Output
The group 3594873 was associated successfully.