CVE-2021-34527 | CVE-2021-1675 - PrintNightmare
This Playbook is part of the Rapid Breach Response Pack.#
Supported versions
Supported Cortex XSOAR versions: 5.5.0 and later.
The playbook can be triggered manually or automatically by setting up a reoccurring job.
Microsoft has released a security update in June 2021 Patch Tuesday for CVE-2021-1675, a Local Privilege Escalation vulnerability in the Print Spooler Service. Later that month, researchers found another method to exploit the Print Spooler service remotely, which raised the severity of the vulnerability due to the fact that the new method allows Remote Code Execution, a new ID was given to the critical vulnerability - CVE-2021-34527.
Microsoft patched the vulnerability in June but an exploit POC and complete technical analysis were made publicly available online.
**Update 7.8.2021 - Microsoft has released an emergency patch for the PrintNightmare. A reference for the patch can be found in "Install Microsoft spooler service patches" task.
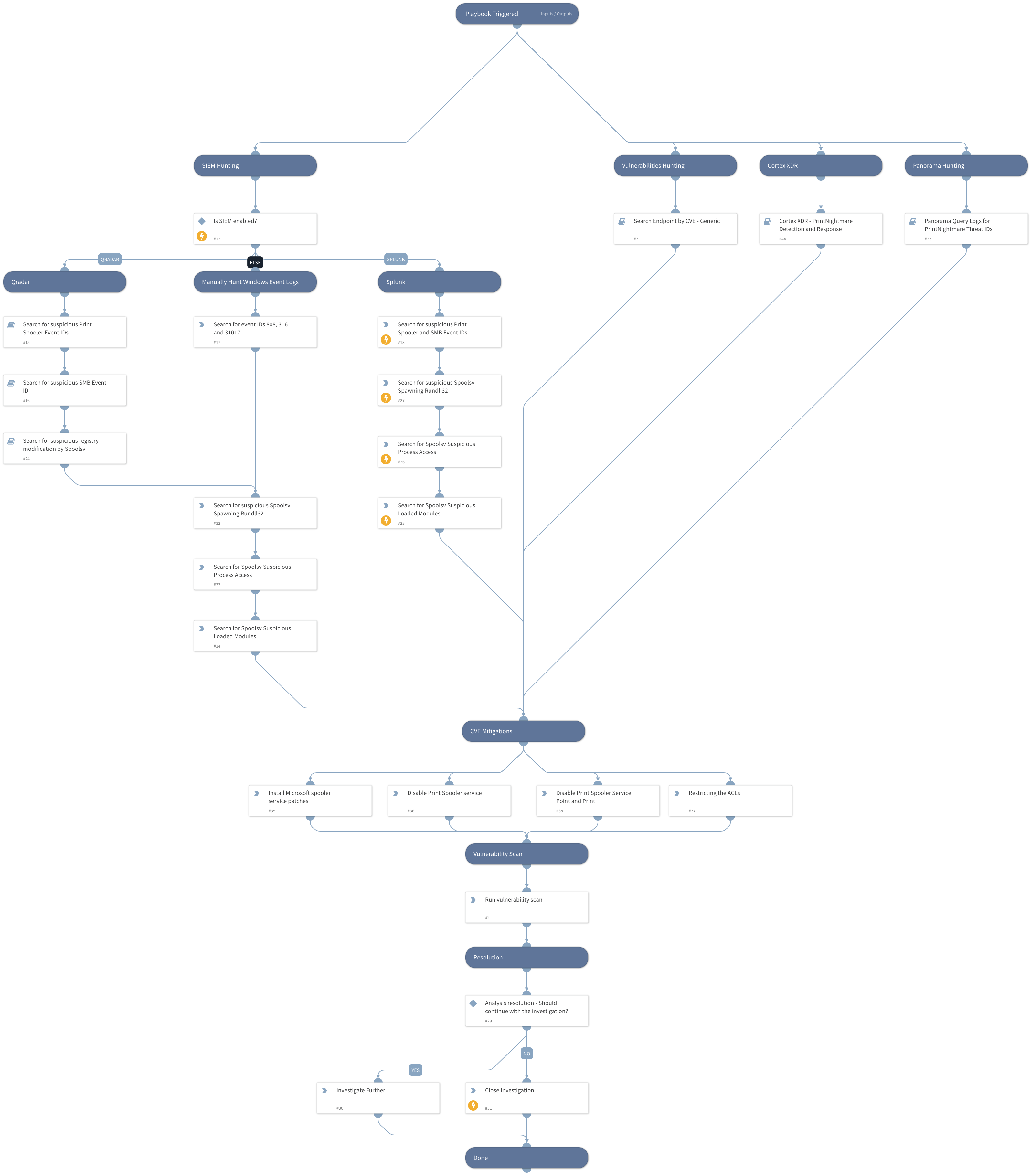
This playbook includes the following tasks:
- Manual actions to mitigate the exploit
- Search Vulnerable Devices using the CVE
- Query SIEM, FW, XDR to detect malicious activity and compromised hosts
- Run Dedicated Detection and Response playbook for Cortex XDR
More details on the vulnerabilities: CVE-2021-1675 LPE CVE-2021-34527 RCE
** Note: This is a beta playbook, which lets you implement and test pre-release software. Since the playbook is beta, it might contain bugs. Updates to the pack during the beta phase might include non-backward compatible features. We appreciate your feedback on the quality and usability of the pack to help us identify issues, fix them, and continually improve.
Dependencies#
This playbook uses the following sub-playbooks, integrations, and scripts.
Sub-playbooks#
- Cortex XDR - PrintNightmare Detection and Response
- QRadarFullSearch
- Search Endpoint by CVE - Generic
- Panorama Query Logs
Integrations#
This playbook does not use any integrations.
Scripts#
This playbook does not use any scripts.
Commands#
- closeInvestigation
- splunk-search
Playbook Inputs#
| Name | Description | Default Value | Required |
|---|---|---|---|
| CVE | PrintNightmare CVEs | CVE-2021-1675,CVE-2021-34527 | Optional |
| SplunkEarliestTime | The earliest time for the Splunk search query. | -30d | Optional |
| SplunkLatestTime | The latest time for the Splunk search query. | now | Optional |
Playbook Outputs#
There are no outputs for this playbook.
Playbook Image#