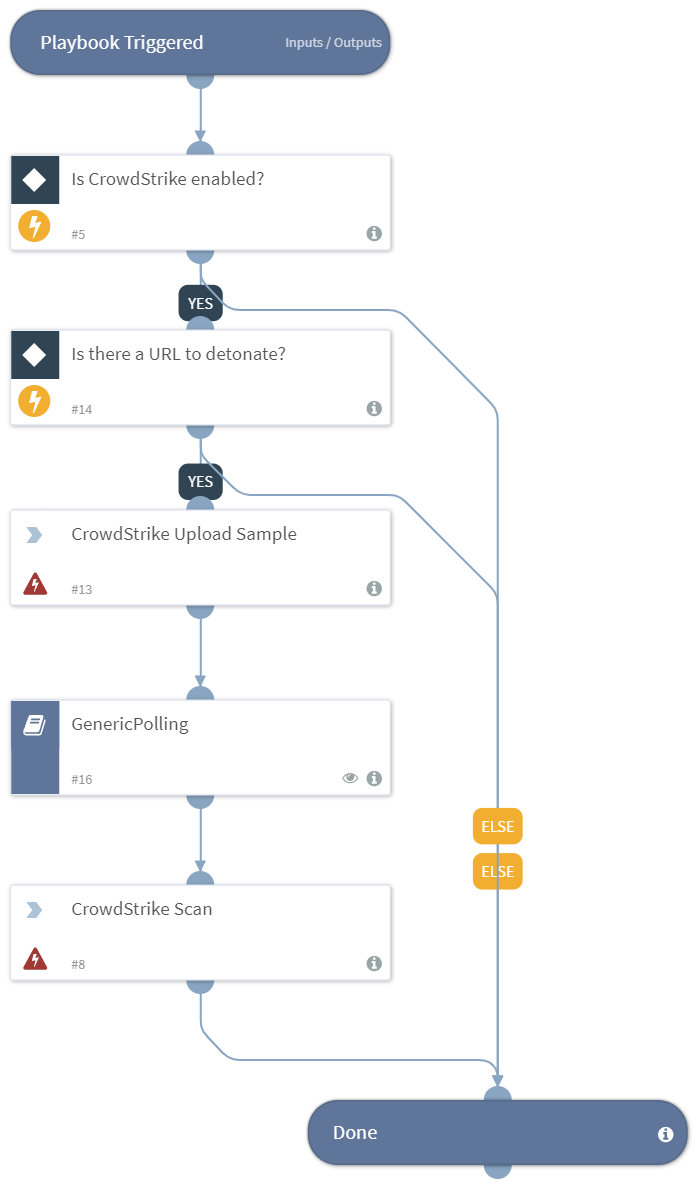
Detonate URL - CrowdStrike
This Playbook is part of the CrowdStrike Falcon Sandbox Pack.#
Deprecated
Use the cs-falcon-sandbox-submit-url command with polling=true instead.
(Deprecated). Use the command cs-falcon-sandbox-submit-url with polling=true instead.
Dependencies#
This playbook uses the following sub-playbooks, integrations, and scripts.
Sub-playbooks#
- GenericPolling
Integrations#
- VxStream
Scripts#
This playbook does not use any scripts.
Commands#
- crowdstrike-scan
- crowdstrike-submit-url
Playbook Inputs#
| Name | Description | Default Value | Source | Required |
|---|---|---|---|---|
| URL | The URL to detonate. | Data | URL | Optional |
| EnvironmentID | The environment ID to submit the file to. To get all IDs run the crowdstrike-get-environments command. | 100 | - | Optional |
| Interval | The polling frequency. How often the polling command should run (in minutes). | 5 | - | Optional |
| Timeout | How much time to wait before a timeout occurs (in minutes). | 30 | - | Optional |
Playbook Outputs#
| Path | Description | Type |
|---|---|---|
| File.SHA256 | The SHA256 hash of the file. | string |
| File.Malicious | The file's malicious description. | unknown |
| File.Type | The file type. For example, "PE". | string |
| File.Size | The file size. | number |
| File.MD5 | The MD5 hash of the file. | string |
| File.Name | The filename. | string |
| File.SHA1 | The SHA1 hash of the file. | string |
| File | The file object. | unknown |
| File.Malicious.Vendor | The vendor that made the decision that the file was malicious. | string |
| DBotScore | The DBotScore object. | unknown |
| DBotScore.Indicator | The indicator we tested. | string |
| DBotScore.Type | The type of the indicator. | string |
| DBotScore.Vendor | The vendor used to calculate the score. | string |
| DBotScore.Score | The actual score. | number |
Playbook Image#